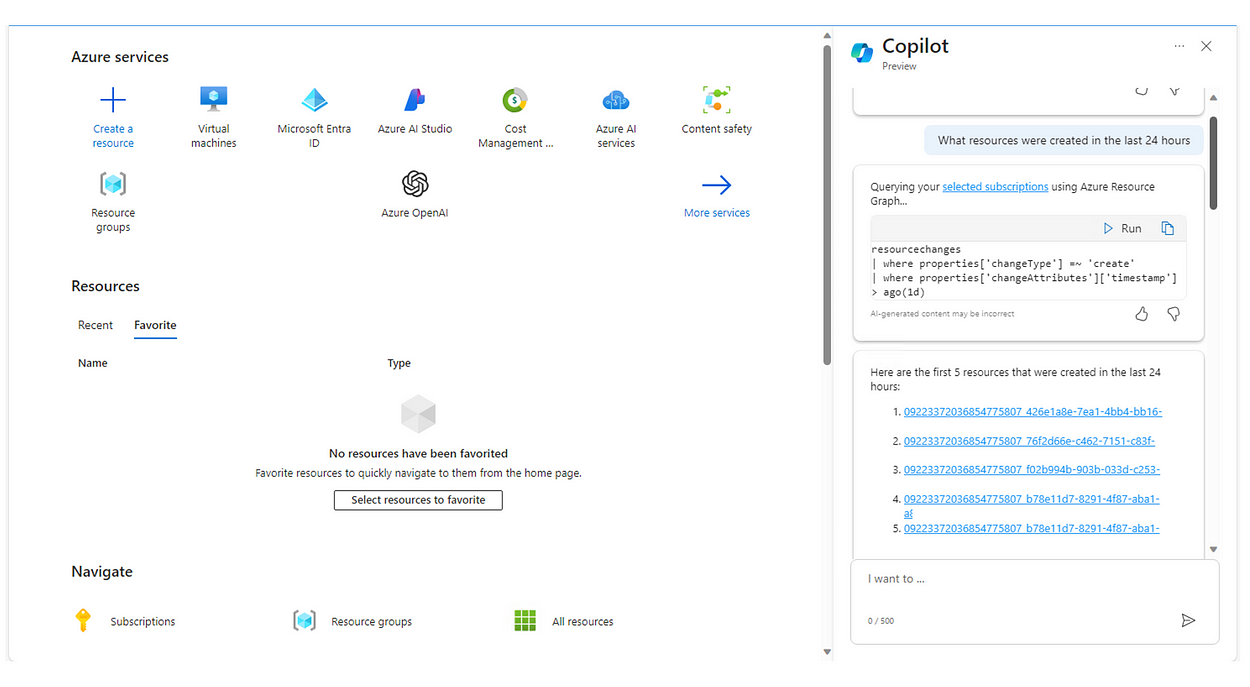
As administrators of an Azure subscription, we are always interested in monitoring what is happening in our environment. To do this, Azure gives us a way to do this through activity logs, which record the actions that are performed on our subscription. These logs can provide valuable information about how the resources are being used and if there are any problems or errors that we should pay special attention to.
In today’s article, I’ll show you how you can use command line tools to get the activity logs for your Azure subscription and how to filter the activity logs to get only what you need.
Important: Remember that Activity log events are retained in Azure for 90 days and then deleted. For information on how to route subscription activity logs to the Azure Log Analytics workspace, see this link
Prerequisites
You must belong to one of these Azure built-in Roles to be able to view activity logs:
- Reader: This role grants read-only access to all resources in a subscription, including activity logs.
- Monitoring Reader: This role lets you view tracking data, including activity logs. Includes read-only access to Azure Monitor, Application Insights, Log Analytics, and metrics in Metrics Explorer.
- Owner: This role grants full access to all resources in a subscription, including activity logs.
- Contributor: This role grants the ability to create and manage all resources, including activity logs.
- Security Reader: This role grants read-only access to Azure Security Center and all security-related data, including activity logs.
Azure PowerShell Workaround#
If you want to know how to install the PowerShell Azure module on your machine, check out this link.
The simplest way to start is to sign in interactively at the command line.
Connect-AzAccount
This cmdlet will bring up a dialog box prompting you for your email address and password associated with your Azure account. If you have more than one subscription associated with your mail account, you can choose the default subscription. To perform this task, we will use the following commands:
Get-AzSubscription
Set-AzContext -Subscription "<subscription ID>"
Once you set your default subscription, you’re ready to start.
Set the variables#
Here we define our environment’s characteristics and the parameters’ values.
$subscriptionID="000000000000-0000-0000-0000-0000000000000"
$endTime = Get-Date
$startTime = $endTime.AddDays(-7)
Get activity log events#
To get the activity logs of your subscription, you should use the Get-AzLog cmdlet with the following syntax; this command allows us to filter the activity logs according to different criteria, such as date and time, severity level, and operation status, among others. Remember that it is also possible to specify an output format that suits us best for our analysis.
Get-AzLog `
-StartTime $startTime `
-EndTime $endTime `
-ResourceId "/subscriptions/$($subscriptionID)" `
-Status Failed `
| Select-object EventTimestamp, Level, Status, OperationName

Parameters & Filters#
- -MaxRecord: You can set the maximum number of activity logs you want to retrieve in the query.
- -ResourceProvider: You can limit the activity logs retrieved to those belonging to a specific resource provider.
- -Status: Allows you to limit the activity logs retrieved to those with a specific status, with the accepted values being success or failure.
- -CorrelationId: You can limit the activity logs retrieved to those related to the specified correlation identifier.
Azure CLI Workaround#
In this case, we will use Azure Cloud Shell, a browser-based shell built into Azure Portal. This allows us to use the Azure command-line tools (Azure CLI and Azure PowerShell) directly from a browser. If you want to know more about Azure Cloud Shell, check out this link. Important: First, you must set up a subscription for the current session.
Set the variables#
Here we define our environment’s characteristics and the parameters’ values.
subscriptionID="000000000000-0000-0000-0000-000000000000"
Get activity log events#
To obtain the activity logs of your subscription, you must use the following command; this command allows us to filter the activity logs according to different criteria, such as date and time, severity level, and operation status, among others. Remember that it is also possible to specify an output format that suits us best for our analysis, such as a table, JSON, or YAML.
az monitor activity-log list \
--offset 7d \
--query "[?contains(subscriptionId, '$subscriptionID')]" \
--status "Failed" \
--query "[].{EventTimestamp:eventTimestamp, Level:level, Status:status.value, OperationName:operationName.localizedValue}" \
--output table

Parameters & Filters#
- --offset: You can set the time range in the format ##d##h. The default value is 6h.
- --max-events: You can set the maximum number of activity logs you want to retrieve in the query.
- --namespace: Allows you to limit the activity logs retrieved to those belonging to a specific resource provider.
- --status: Allows you to limit the activity logs retrieved to those with a specific status, with the accepted values being success or failure.
- --correlation-id: You can limit the activity logs retrieved to those related to the specified correlation identifier.
Thanks for reading my post. I hope you find it useful.
If you want to know more about Azure Monitor Activity Logs, check out this link